Senuwan W.M.D
it21118036@my.sliit.lk
Tracking Users’s Location While Preserving Privacy
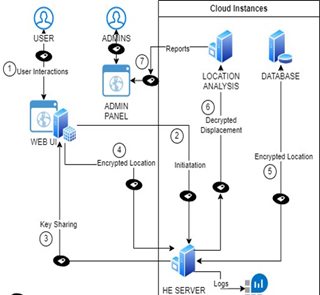
The architecture of the proposed LBS consists of the following components, “USER” is the endpoint where users interact with the interface, services will request the longitude and latitude of the user, and the user will be provided with encrypted location data. There is a process that needs to be followed before data encryption, to encrypt data using HE, data needs to be encoded. There are several methods to perform encoding. However, the use of HE and CKKS (Cheon-Kim-Kim-Song) schemes limits these options. When considering SEAL Libraries, it was developed to support Single instruction/Multiple Data (SIMD). This utilized parallel processing which enables more efficient operations. Native encoder which was embedded in the library supports this technology. This can be utilized for recurring updates of user location flows. It is suitable for the proposed system, as it can be scaled up depending on the consecutive requests that were received by the server to perform, HE functions. After which cipher context of the algorithm must be initiated. The cipher context includes values, parameters, and arguments that will be used to initialize the HE processes successfully. Before selecting these parameters, encryption requirements must be thoroughly analyzed. This includes the purpose, data that are being used, plaintext data types, and storage requirements. It is a vital step since the cipher context is initialized based on these requirements.
Values are considered integers or chars. The remaining float values will be rounded to base 20 to get the integer. Since the location values are in the float format, the CKKS scheme is used as the encryption scheme as the value is not fixed and float values are used. However, there was considerable storage overhead associated with the CKKS scheme compared to BFV (Brakerski-Fan-Vercauteren), even though the CKKS scheme is the only scheme that can operate on the real number domain. It possesses many capabilities compared to BFV. The polynomial modulo and its related coefficient modulo are adjusted according to performance and accuracy. Secure communication channels such as HTTPS will be used for transmitting encrypted location data to the HE server. HE server at the backend that received encrypted location data will store the data in the HE database. The database can be utilized to process data for computation on it. Any algorithms that are optimized or built with the CKKS scheme are compatible with this. The current scheme supports addition and multiplication operations. This is facilitated by the evaluator function in the library. Since these values are encrypted, the leakage of such a database can result in no harm for most of the part as homomorphic encryption is a quantum resistance encryption. Following up, unlike encrypting a whole database to a different cipher context will create a severe processing load on the system.
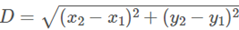
The Computation module will perform computations and will be presented to the analytics module to analyze displacement and anomalies. The technique used for displacement computation is based on the Euclidean Distance Formula [15] (1), “D” is the Euclidean distance while “x” represents the Longitude and “y” represents the latitude. Moreover, x1, y1 will be the initial geo-location details, and x2, y2 will be the second geo-location details (1). Therefore, considering every last decimal bit was very important when considering obtaining longitude and latitude values, as we are processing this information to detect anomaly detection of users based on their location. However, computing on the set of the same data locations as the consumers will be at rest can generate noise, which is also known as the “Noise Factor”. This is addressed, with the use of the “Relinearization” methodology. Moreover, there were methodologies such as “Bootstrapping”, which was compared to the current method allowing a more reduced and refreshed budget which can be less in size compared to Relinearization operation. However, it hasn’t been implemented in SEAL, which is for future developmental improvements, as it is in the SEAL’s roadmap for CKKS. That being highlighted, implementing bootstrapping can cause a significant performance hit, often a large magnitude in resource usage. Considering the requirement for the process requires accuracy, this is highly important and must be taken into consideration for future developments
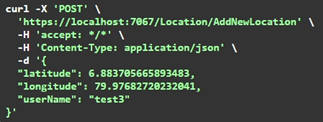
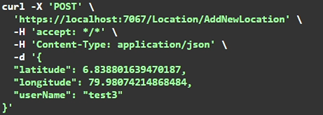
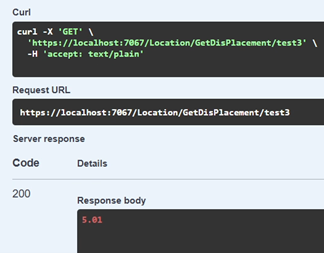

The research also presented an efficient HE-based method to solve security challenges in Location-Based Services (LBS) while ensuring user privacy gets preserved but still offering efficient services
The figures illustrate an example use case, between the Athurugiriya Interchange (Location based in the western region of Sri Lanka) and the Hiripitya Road Interchange (Location based in the western region of Sri Lanka), which is almost a linear road stretch of 5.1km on Google Maps. As we are calculating displacement, the above value depicted in Fig.5 has a similar accuracy to the similar tests conducted, giving an average accurate rating of 98.9%, relative to the distance shown by Google Maps.
These studies demonstrated how integrating state-of-art machine learning algorithm such as the Random Forest classifier with other state-of-art cryptographic as well as authentication methods. This integration also improved cloud-based VDI security and paved the way for other advancements in the field of cybersecurity and privacy
Technologies
Here are some of the technologies that was used to develop the system