Dissanayake D.S.N.N
it21097560@my.sliit.lk
Secure Authentication Using ZKP Protocol
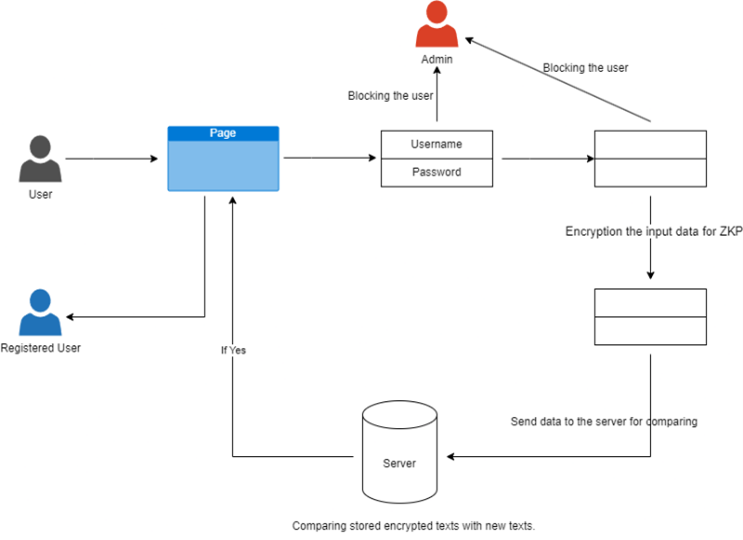
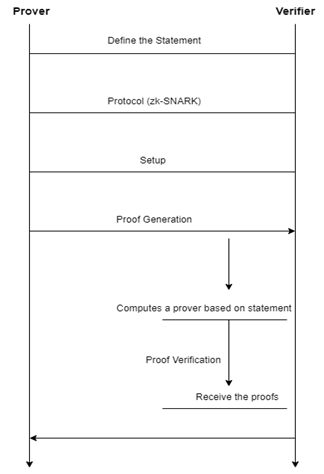
The users can log into the web app with their username and password as designated by the user before being authorized to use it. That is the same way we secure other Sites and applications. There is then the provision of subsequent layer and additional security measures set up as the users will be required to provide answers to some secret question as a pre-selected security measure. That way, two-factor authentication introduces another layer of security and makes personal data more protected since users should verify their identity via the separate channel. To complement security and protect user privacy, identity checks are proposed by Zero-Knowledge Proof modality authentication within the provided responses and the user login as well. [2] This acquisition test leads the holder of the key and the user to confirm the authenticity of the user's secret information without passing on the actual security questions to the user. It is a way for the server to verify the authenticity of the user. By virtue, thus of this act, data other than sensitive information is shared with the server, but such (sensitive) information remains confidential. It happens that after a successfully processing of a ZK-Proof the API call will be carried out, allowing a user to fellow the application Robust security features such as encryption and hashing of individual accounts data form the basis on which other safeguards are developed to counter threats of unauthorized access to the information. Regular audits and updating security protocols are also crucial for the protection of the authentication process, as this offers a means to improve the integrity and efficacy of the security measures over time, ensuring that the system continues to defend against the new security risks and vulnerabilities.
To be able to properly utilize ZKP as an authentication process, it should start with clearly laying out the specific authentication criteria closely related to the system. Address this by stipulating the types of secrets that are accessed and the security level clients need. [3] After setting the needs to the authentication procedures, the next step is to choose a ZKP protocol which complies with these terms. The level of the security (a factor) desired, the computational efficiency (another factor) and the complexity of the authentication process (the third factor) affect this decision. After that, the system chooses the ZKP protocol, it is creating needed parameters or keys for this protocol's further implementation. The implementation can be seamlessly integrated into the user registration process, and it will not interrupt the user registration process, ultimately resulting in a better onboarding user experience. The next step is the users initiating authentication process by producing proof which attests to own possession of the secret information, passwords or cryptographic keys, for example. These proofs go to authentication system which is perfectly independent and compares them for confirmation. Once the validation process of the proofs was successful, access will be given to the authenticated user that will allow them to utilize the facilities or services of the platform. These security inspections and audits are needed to prevent changes in the authentication process that might result in compromised security and data integrity. Thus, such attempts ensure that the dangers are detected and dealt with in due time to prevent the system from being breached accidentally or purposely. In the end, the algorithm based on zero-knowledge proof is implemented and executed across the platform as a guarantee of constant, safe user authentication. This way, the system becomes not only highly effective and efficient in authentication but also user-oriented, considering security and privacy as its major points.
Technologies
Here are some of the technologies that was used to develop the system